VPC (Virtual Private Cloud) allows you to create virtual networks within AWS. This allows you to logically separate resources, add additional security, configure networking attributes (such as routing tables etc) along with build VPNs from your remote site into your AWS solution.
Each AWS account comes with a default VPC. Within this VPC subnets are all assigned to an internet gateway. It is also worth mentioning you are unable to recover a deleted default VPC.
VPCs are configured on a per region basis. A maximum of 5 VPCs can be configured within a single region.
Table of Contents
VPC Components
There are various components within VPC. These components are separated into,
- VPC – General VPC components such as routing, subnets, Elastic IPs etc.
- Security – Consists of controls to permit/restrict traffic from/to your AWS resources.
- VPN – Allows you to build VPN tunnels into AWS, from your remote sites.
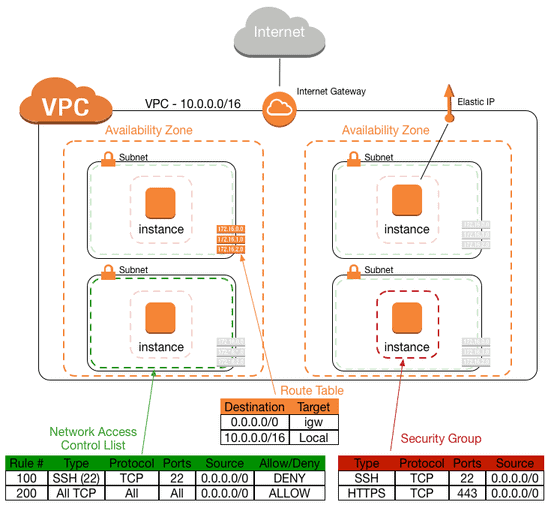 Example VPC Topology
Example VPC Topology
VPC
Subnet – A subnet is a sub network of a larger network. Within VPC a subnet is mapped to a single availability zone. Subnets are associated within routing tables along with EC2 instances.
Route Tables define how traffic is routed within your VPC. This is achieved via a combination of routes and subnet association. Each VPC has one ‘main’ routing table, by default.
Internet Gateways – Once an Internet Gateway is created it is associated within the routing table to publicly route traffic. Only one IGW can be assigned per VPC.
DHCP Option Sets allow you to define the configuration parameters of DHCP. Once a DHCP Option Set has been created you can then assign it to your VPC.
Elastic IPs are simply a public IP address that can be assigned to any instance or network interface within your VPC. In turn allowing your to migrate the IP to other AWS instances in the event of failure.
Elastic Network Interfaces can be moved from one instance to another. MAC and IP addresses are associated to an ENI. Their use is best suited in redundancy/failover based solutions.
Endpoints provides direct communication to other AWS services without the need to publicly route or VPN the traffic. Currently Endpoints only support the S3 service.
NAT Gateways allow you to SNAT traffic behind a single elastic IP.
Peer Connection provides the ability to connect 2 VPCs together. The VPCs can be with the same account or within another AWS account. The key caveats are,
- VPCs must be in the same region.
- VPC peering is performed in a star based topology. Transitive peering is not supported. This means sending traffic from VPC A to VPC C cannot transverse VPC B. Instead VPC A and VPC C must be peered.
- CIDRs must not overlap between VPCs.
Security
Security Groups provide access-control at the EC2 instance level. Additionally,
- Only allow rules can be configured.
- Rules are stateful.
- By default,
- All INBOUND is denied
- All OUTBOUND is permitted
- Changes take effect immediately
Network Access-Lists provide access-control at the subnet level. Additionally,
- Both allow and deny rules can be configured.
- Rules are stateless
- Override security groups
VPN
Customer Gateways define the remote peer within your encryption domain.
Virtual Private Gateways are routers on the AWS side of the VPN tunnel. I.e the local peer within the encryption domain. Only one VPG can be associated to a VPC.
VPN Connections bind both the Customer Gateway and Virtual Private Gateway.
Direct Connect
Direct Connect allows you to build a connection into your VPC using a dedicated leased line, rather then transversing the internet.
This works by provisioning a dedicated line from the customer site to a Direct Connect facility. Within this facility a Cross Connect is then run from the lease line termination point into the AWS Infrastructure. From there AWS then connects you into one of there AWS datacenters via darkfibre.
Connections speeds range from sub 1Gb to 10Gb, and both Dot1q tagging/BGP is used for layer2/3 connectivity.
The main benefits are,
- Reduction in costs for large traffic volumes.
- Improved reliability.
- Greater bandwidth.
How is this different from a VPN ?
VPNs are quickly configured, they provide average bandwidth constraints and are prone to the inherent issues when running traffic over the internet.
However Direct Connect runs across dedicated private connections, rather then the internet. This provides greater stability and performance over a VPN based connection.
Sources
Image : https://aws.amazon.com/blogs/apn/amazon-vpc-for-on-premises-network-engineers-part-one
- Fortinet– How to configure NTP on FortiGate - January 13, 2026
- How to Configure a BIND Server on Ubuntu - March 15, 2018
- What is a BGP Confederation? - March 6, 2018
Want to become a certified AWS expert ?
Here is our hand-picked selection of the best courses you can find online:
Ultimate AWS Certified Cloud Practitioner course
Ultimate AWS Certified Solutions Architect Associate course
Ultimate AWS Certified Developer Associate course
and our recommended certification practice exams:
AlphaPrep Practice Tests - Free Trial
