Table of Contents
What is AFM ?
Introduced within 11.3, AFM (Advanced Firewall Manager) is a licensed module for the BIGIP appliance that provides stateful firewalling along with reporting and DoS protection.
Within this article we will look at AFMs key components and also how it processes traffic.
Contexts
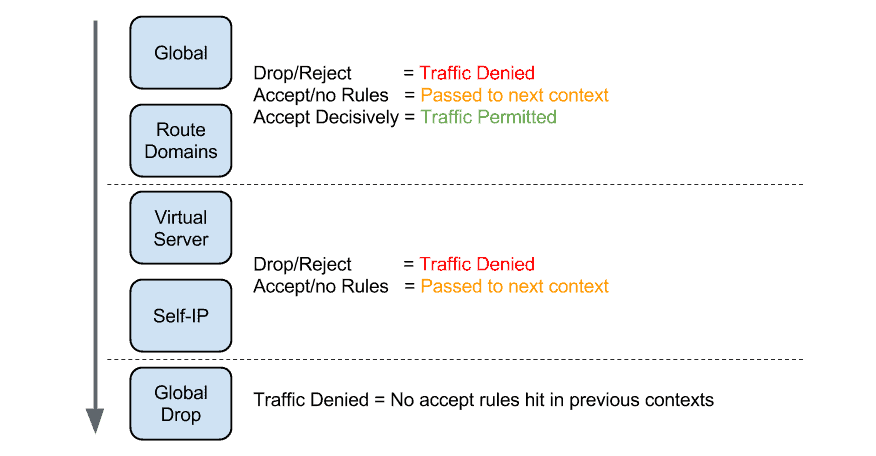
A context defines the scope of a firewall rule. In other words the category of object to which the rule applies. In total there are 6 contexts. They are,
- Global
- Route Domain
- Virtual Server
- Self IP
- Management IP
- Global Drop
Actions
When creating rules there are 4 main actions. However depending on the context the actions differ. The 4 actions are :
- Accept – The packet is allowed to pass the rule, and is then passed to the next context for processing.
- Drop – The packet is silently dropped.
- Reject – A RST is sent back to the client if TCP is used. Otherwise an ICMP unreachable is sent.
- Accept Decisively – The packet is permitted i.e no further context processing is performed.
Each of the contexts allow for the actions Accept, Drop and Reject. However the Global and Route Domain contexts also include the Accept Decisively action.
Processing Order
To understand the processing order there are some key points you must be aware of,
- Each context has a order of preference when a packet is processed by the AFM.
- There are 2 Deployment modes. This is configured via the ‘Default Firewall Action’ option within ‘Security / Options / Network Firewall’. The settings are shown below,
- ADC – Virtual Server & Self IP Contexts = Accept ; Global Context = Drop (Default)
- Firewall – Virtual Server & Self IP Contexts = Drop or Reject ; Global Context = Drop
- The Global Context action is not configurable.
- If a packet hits a context with an action of Accept, the packet is then passed onto the next context and negates the Global Drop context.
- If a packet hits the Global or Route Domain context with an action of Accept Decisively the packet negates any further processing and is sent onto the destination.
- The Management IP context is processed independently of the other contexts including the Global and Global Drop contexts.
Network Firewall
The AFM’s key feature is its ability to act as a network based (stateful) firewall. In order to understand the various options available we will describe the functions and key components within the AFM Network Firewall.
- Active Rules / Policies – To permit or deny traffic you can either use Active Rules or Policies. Below shows the differences,
- Active Rules – Can be assigned across all contexts.
- Policies – Can be assigned across all contexts. However Policies can also be assigned to a Virtual Server and applied in staging mode only (i.e do not perform an action only log).
- Rule Lists – A Rule list, as the name suggests. Is a collection of rules.
- IP Intelligence – IP Intelligence allows you block traffic based on an IP black list. This list is retrieved either directly from F5 (an additional license is required) or you can use your own custom feed.
Security Protocols
Where as the Network Firewall allows you to block (or permit traffic) at the transport layer (i.e layer 4). Security protocols allow you block traffic based on certain conditions within the protocol itself. There are 2 protocols that can be configured. They are, DNS and HTTP.
To configure ‘Security Profiles’ a security profile is configured which is then assigned to the Virtual Server. Here are the steps,
- Create a ‘Security Profile’ via ‘Security / Security Protocols / DNS or HTTP’.
- HTTP – Within the Virtual Server. Assign the Security Profile within the Security tab.
- DNS – Create a DNS. Enable DNS Security and assign the Security Profile within this profile. Assign the DNS profile to the Virtual Server.
DoS Protection
DoS Protection can both alert and block network based attacks. Within DoS Protection there are 3 key components – DoS Profiles, Device Configuration and White Lists.
DoS Profiles
DoS Profiles act to only alert should the thresholds within the DoS Profile be reached. These thresholds can be configured for either DNS or SIP. Once the DoS Profile is configured it is assigned on a per Virtual Server basis from within ‘Local Traffic / Virtual Servers / Virtual Server List / Security Profiles / DoS Protection Profiles’.
Device Configuration
AFM, by default, blocks common network based attacks such as ARP Floods, Fragmentation attacks etc. Within AFM each of these attacks have a set of thresholds that can be adjusted. These thresholds define the point at which the AFM should either alert or block the attack. These thresholds are located within ‘Security / DoS Protection / Device Configuration’.
The descriptions of the thresholds are shown below,
- Detection Threshold PPS – Defines the threshold (Packets Per Second) for when the AFM detects an attack.
- Detection Threshold Percent – Defines the percentage of ‘Detection Threshold PPS’. Once reached AFM drops all packets exceeding this threshold percentage.
- Default Internal Rate Limit – Defines the total packets per second allowed. Any packets above this are dropped.
Single Endpoint Attack
Within the DoS Device Configuration there is an option to configure the thresholds for Single EndPoint Attacks. In my opinion these are 2 most useful mitigation options.
The 2 options that can be configured are,
- Sweep – Protects against a sweep attack from a single Source IP.
- Flood – Protects against a flood attack from multiple Source IPs.
White Lists
As the name suggests While Lists provide the ability to negate DoS protection for certain traffic.
White lists are applied to all traffic except for traffic tranversing the management interface and can be processed in in either software or hardware. Non ePVA platforms process whitelists in software whereas ePVA platforms process the whitelists in hardware. However because of this hardware implementation there is a maximum limit of 8 white list entries.
To configure a white list goto ‘Security / DoS Protection / White Lists’
Logging
AFM can be configured to either log locally or to send logs to a remote log server. There are 3 main components to logging. They are,
- Logging Profile – Defines what to log. Configured via ‘Security / Event Logs / Logging Profiles’
- Log Publisher – Is a container for ‘Log Destinations’, shown below. Configured via ‘System / Logs / Configuration / Log Publisher’
- Log Destination – Defines where to send the logs. Configured via ‘System / Logs / Configuration / Log Destination’
In order to configure logging the Log Destination is assigned to the Log Publisher. The Log Publisher is then assigned to a Logging Profile. This Logging Profile can then be assigned to contexts (i.e Virtual Servers). Otherwise you can simply turn the profile on or off from within a global rule.
Commands
| Command | Details |
| show security dos device-config all | shows hit counts for dos device configuration |
Caveats
- Packet Filters – In the event of both packet filters and AFM being enabled. Packet filters will be processed first.
- iRules – If an iRule is assigned to a global rule then the rest of the global rule will not be processed.
Links / References
- How to Configure a BIND Server on Ubuntu - March 15, 2018
- What is a BGP Confederation? - March 6, 2018
- Cisco – What is BGP ORF (Outbound Route Filtering)? - March 5, 2018
Want to become an F5 Loadbalancers expert?
Here is our hand-picked selection of the best courses you can find online:
F5 BIG-IP 101 Certification Exam – Complete Course
F5 BIG-IP 201 Certification Exam – Complete Course
and our recommended certification practice exams:
AlphaPrep Practice Tests - Free Trial
