What is SNI? SNI (Server Name Indication) is an extension to the TLS protocol, that provides the ability to host multiple HTTPS-enabled sites on a single IP. How does it work? Prior to SNI the client (i.e browser) would send the requested hostname to the webserver within the HTTPS payload (Figure 1). Due to the … Read more
What is ATS ? Introduced within iOS9 and OS X 10.11, App Transport Security (ATS) is a new feature that enforces greater security within Apples application libraries. This means that when an application makes an connection, using the NSURLConnection, CFURL, or NSURLSession libraries, that the connection must meet the following requirements. The server must support … Read more
HTTP Strict Transport Security (HSTS) is a security policy based on RFC9767 designed to protect domains against both downgrade and passive network attacks. HSTS achieves this by, Transforming all insecure (HTTP) based links to HTTPS links. Allowing the browser to terminate the connection should it observe any certificate warnings or errors with the domains certificate. … Read more
A cipher suite is a set of algorithms used within a SSL/TLS session to provide data integrity, authentication and confidentiality for communication between a client and a server. Each cipher suite contains a, Key Exchange algorithm – Used in the creation of a secret key which is used within the bulk encryption process. Also known … Read more
There are times where you may require your webpages to be password protected. To achieve this within Apache the usernames and passwords are stored within a flat file called htpasswd. This is then referenced within your Apache configuration. Configure Apache Within your .htaccess file configure the following. AuthType Basic AuthName “restricted area” AuthUserFile /var/www/html/website/.htpasswd require … Read more
Introduction Certificate Revocation is used within PKI (Public Key Infrastructure) to instruct the client that the certificate can no longer be trusted. This is required in scenarios where the private key has been compromised. Certificate Types Prior to a CA issuing a certificate to a company the CA performs a level of validation on the … Read more
By: Ayman Hammoudeh Introduction Pivoting refers to method used by penetration testers that uses compromised systems to attack other systems on the same network to avoid restrictions such as firewall configurations, which may prohibit direct access to all machines. For example, an attacker compromises a web server on a corporate network; the attacker can then … Read more
What is Incapsula ? Incapsula is a cloud based service that provides the ability to add further security and also improve the performance of any website in a matter of minutes via a few simple DNS changes. How does it work ? Incapsula works by routing traffic via its global CDN network prior to … Read more
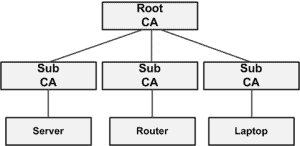
Purpose The main purpose of this document is to explain the PKI term ‘Chain of Trust’. Summary PKI (Public Key Infrastructure) is a framework built upon protocols, services and standards used to provide authentication, confidentiality, integrity, non-reproduction and access control to digital data. The term ‘Chain of Trust’ is used to describe the trust relationship … Read more
Digital Signatures A Digital Signature is a method to ensure data authenticity. A digital signature is created by generating a hash (message digest) against the data and then encrypting this digest using the cryptography (public or private) key. This signature is then appended to the data. Once the recipient has received the data + signature … Read more
There are 4 main types of IDS alerts. These are : True Positive Bad traffic which triggers an alert. False Positive Good traffic which triggers an alert. False Negative Bad traffic, but no alert is raised. True Negative Good traffic, and no alert is raised.
Horizontal Scan A horizontal scan is described as scan against a group of IPs for a single port. Vertical Scan A vertical scan is described as a single IP being scanned for multiple ports. Box Scanning A combination of both vertical and horizontal scans.
Web services rely on the transfer of XML data. This poses a threat from the point of view that every packet possible could be malicious. Hackers may send SOAP (Simple Object Access Protocol) packets containing executable messages, crafted windows/SQL executables within XML packets or even initiate a XDoS (XML DoS attack). As the name suggested … Read more
SPAM Spam continues to be the major threat affecting email systems today. The term Spam is used to define junk email messages that are usually sent out in high volumes to thousands of users at a time. SPAM Invasion Below contains some examples of some HTML-based filter evasion tactics, Tiny or invisible text that is … Read more
Want to become an IT Security expert?
Here is our hand-picked selection of the best courses you can find online:
Internet Security Deep Dive course
Complete Cyber Security Course – Hackers Exposed
CompTIA Security+ (SY0-601) Certification Complete course
and our recommended certification practice exams:
AlphaPrep Practice Tests - Free Trial